III. PRECAUTIONS FOR WINDOWS USERS:
a) Remember the most basic rule: Don't open file attachments
unless you have some way of knowing that they are legitimate.
(If you're saying to yourself, "duh, of course!" then skip ahead
to II.b.)
What does that mean, exactly? Here are some examples:
o If it is a program, and the sender didn't write it himself,
don't run it, period. If someone sends you a "fun" program
or screensaver that they "found" somewhere, do not open it.
It doesn't matter whether they tried it or not -- these things
can contain "time bombs" so that they appear to work as
advertised for a while before doing their damage, so testing
it cannot prove that it is safe.
o If the file attachment comes from a stranger, you cannot know
that it is legitimate, so don't open it.
o If it appears to be from someone you know, but there's nothing
to prove that it is really from him, then you can't know that it
is legitimate, so don't open it. Worms/viruses routinely forge
email headers, so most computer worms & viruses that you will
receive will appear to be from someone you know.
o On the other hand, if your colleague told you on the phone,
"I'll send you the JPEG picture this afternoon," and, as promised,
it shows up, it is pretty safe. (But avoid Word .doc files and
Excel .xls files if possible, since they occasionally contain
macro viruses.)
o Or if the email contains identifying information that could
not have been written by a stranger (e.g., if it is signed,
"your little brother, Frank"), it is probably safe.
b) Some common viruses, such as Badtrans, Klez & Yaha, exploit flaws
in the Outlook Express "preview pane" feature to run automatically,
without being explicitly opened.
A good remedy is to use a non-Microsoft email client, such as
Eudora, Pegasus Mail, or the Mozilla mail client, instead of Outlook
Express or Outlook. Pegasus and Mozilla are free, and Eudora is
free for personal use.
Users of Outlook Express (or Outlook) should make the following
setting change to prevent viruses like Badtrans from running
automatically when email is viewed in the Outlook Express or
Outlook preview pane.
First you need to start Outlook Express or Outlook (not Internet
Explorer). Then set:
Tools -> Options -> Security -> Restricted Sites Zone
(Note: some newer computers with pre-installed software
might come with this set by default, which is good.)
(This applies to Outlook Express 5.0-6.0, and to Outlook 98. There
are probably similar settings that need to be adjusted in other
versions of Outlook, but I don't know whether they are identical.)
Also, with some versions of Outlook Express and Internet Explorer
5.xx, it might be necessary to make an additional setting change,
in Internet Explorer:
Internet Explorer 5.xx:
Tools -> Internet Options -> Security ->
Restricted Sites -> Custom Level ->
Downloads / File Download -> Disable
(Note: if it was already disabled, that is good.)
This won't protect you if you "open" an infected executable email
attachment. So don't! Most people should never need to open any
attachments except .jpg or .jpeg files (photos), and perhaps .rtf
or .txt files (documents).
Also, the same rules apply when someone sends you a file via IRC.
Some viruses spread that way, too.
However, Windows' default file viewing options can hide the true
file extension, so that you can be fooled into opening a .com, .exe,
.doc, .xls, .xlw, .vbs, .bat, .pif, .scr, or other infected file
if it is named "file.jpg.exe" or similar. Until you change the
option, Windows hides the last dot and extension, supposedly as a
"user-friendly" feature. To reduce your likelihood of being fooled,
change the option:
First, start Windows Explorer or Windows NT Explorer, then find
the Options menu item under either View or Tools. Then select the
"View" pane. Then uncheck the checkbox option labeled "Hide file
extensions for known file types" or similar, or click the radio
button for "Show hidden files and folders." (Microsoft seems to
rearrange and reword the menus in every new version of Windows):
Windows Explorer or Windows NT Explorer:
Tools -> Folder Options -> View ->
(or: View -> Options -> View -> )
then select Show hidden files and folders
or uncheck Hide file extensions for known file types
or uncheck Hide MS-DOS file extensions for file types that are registered
Unfortunately, changing the option does not work for .pif files.
You can see for yourself, by performing a little experiment:
1) Copy an innocuous program file, like calc.exe, to c:\ (or some
other suitable location), and rename it to README.TXT.pif
2) Run Windows Explorer or Windows NT Explorer and view the files in c:\
3) Note that README.TXT.pif is shown as README.TXT
4) Double-click on it, and see that the program (calc.exe) runs
If that program had been a malicious file attachment, it could
have wiped out your hard disk drive! (Thank you, Microsoft.)
But there is a subtle visible clue, which can tip you off about
the threat. Look again at "README.TXT" (really README.TXT.pif) in
Windows Explorer. Note the "MS DOS" shortcut icon  (or
(or  ) beside
it (or, under Win95, a plain "shortcut" icon). That's the clue,
indicating that it is an executable program. If it had really been
a text file, it would have had a Notepad icon
) beside
it (or, under Win95, a plain "shortcut" icon). That's the clue,
indicating that it is an executable program. If it had really been
a text file, it would have had a Notepad icon  beside it.
So: BEWARE of files with MS DOS icons,
beside it.
So: BEWARE of files with MS DOS icons, 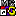 or
or  -- they are executable
programs, regardless of the apparent file extension. Do not
open them!
c) There are some truly hideous bugs in Microsoft's email and
browser products, some of which let attached viruses run automatically
when the email is viewed either manually or in the "preview pane,"
even if Outlook Express is configured for the "Restricted Sites Zone."
Fortunately, Microsoft has fixes available, but that won't help you if
you don't have them. So, if you use Microsoft Internet Explorer 5.xx
or 6.0, and especially if you use Outlook or Outlook Express, it is
very important that you apply the latest security and "cumulative patch"
(formerly "security rollup") fixes.
The most important fix included in the latest "Cumulative Patch"
is MS01-020, which fixes a critical bug exploited by Klez. For
details of how that bug works, see microsoft_mime_bug.txt.
Note: for a nice table of older Microsoft security fixes, see:
http://www.zianet.com/bwd/securitybulletins.asp
Unfortunately, it is not very up-to-date.
If you use Internet Explorer 6.0, then you need to install the MS02-047
"Cumulative Patch." (See details below.)
If you use Internet Explorer 5.5, then you need to first make sure
that you have either SP1 or SP2 installed, then install the MS02-047
"Cumulative Patch." (See details below.)
If you use Internet Explorer 5.01 under Windows 2000, then you need to
first make sure that you have IE 5.01 SP2 installed, or Windows 2000 SP3
installed (which also installs IE 5.01 SP3). Then install the MS02-047
"Cumulative Patch." (See details below.)
If you use Internet Explorer 5.01 under any operating system other than
Windows 2000, you cannot use MS02-047, so you must instead use the
earlier MS02-015 "Cumulative Patch," (see details below). Or, better
yet, upgrade to Internet Explorer 5.5 or 6.0. But if you insist on
sticking with IE 5.01 under Win-9x/Me, first make sure that you have
IE 5.01 SP2 installed, then apply MS02-009 and MS02-015 (details below).
Note: Internet Explorer 5.00 and earlier are no longer supported by
Microsoft, and Internet Explorer 5.01 is only supported on Windows 2000.
However, if you are running IE 5.01 or IE 5.5, then you might need to
apply a "Service Pack" before you can apply the "Cumulative Patch."
Note: to check which service packs are already installed, start Internet
Explorer and click on Help -> About, and look at the "Update Versions"
line. If you see "SP1", "SP2" or "SP3" then you already have Service
Pack 1, 2 or 3, respectively, installed in your copy of Internet
Explorer.
If you are running IE 5.01, you must first apply Service Pack 2 (SP2),
unless it is already installed, before you can apply the Cumulative
Patch update. If you are running IE 5.5, you should first apply SP2
unless either SP1 or SP2 is already installed.
For IE 5.5, if you don't already have either SP1 or SP2 installed, then
get SP2 here:
http://www.microsoft.com/Windows/ie/downloads/recommended/ie55sp2/default.asp
or here: http://support.microsoft.com/default.aspx?scid=kb;en-us;Q276369
For IE 5.01, if SP2 is not already installed, then get it here:
http://support.microsoft.com/default.aspx?scid=kb;en-us;Q267954, or here:
http://www.microsoft.com/Windows/ie/downloads/recommended/ie501sp2/default.asp
For IE 6.0, there are no Service Packs (yet).
Then for IE 5.5 or IE 6, or for IE 5.01 under Windows 2000, apply
MS02-047 (a/k/a Q323759), about 2-2.5 MB (~8-15 minutes to download
with a typical dial-up modem):
http://www.microsoft.com/windows/ie/downloads/critical/q323759ie/default.asp
Or for IE 5.01 under Win-9x/Me or NT 4, apply MS02-009 (a/k/a q318089),
about 300 KB (~2 minutes to download with a typical dial-up modem):
http://www.microsoft.com/technet/security/bulletin/MS02-009.asp,
then apply MS02-015 (a/k/a Q319182), about 2-2.4 MB (~8-15 minutes
to download with a typical dial-up modem):
http://www.microsoft.com/technet/security/bulletin/MS02-015.asp
Note #1: Microsoft fixes should generally be applied in chronological
order, according to the dates on which they were released.
Note #2: Unless you are running Windows XP, when applying two or more
Microsoft fixes which prompt you to reboot the computer, you really
should let it reboot the computer after each one. Or, with NT 4 or
Windows 2000, you may apply them all and then run Microsoft's
QChain.exe utility before rebooting the computer. Get QChain here:
http://support.microsoft.com/default.aspx?scid=kb;EN-US;q296861
d) All Windows 9x/ME/NT/2K/XP users should apply these Microsoft
Java/VM updates:
http://www.microsoft.com/technet/security/bulletin/ms02-013.asp
http://www.microsoft.com/technet/security/bulletin/ms02-052.asp (Q329077)
MS02-013 is 4.3 MB. Fortunately, MS02-052 is only 168 KB, so it
is a quick download. Unfortunately, even though Microsoft says that
these fixes are "critical" for users of all versions of Windows
9x/Me/NT/2K/XP, they now seem to be only available through Microsoft's
cumbersome "Windows Update" facility (search for "Q329077"), which
only supports Windows 2000 & XP. There probably is some way for
Win 9x/Me users to get the fixes from Microsoft's web site, but I
haven't figured out how. Perhaps you can just lie about what version
of Windows you are using?
MS02-052 is apparently the same for all versions of Windows, and it
can also be downloaded as vm-sfix3.exe (Q329077) - 167,168 bytes from
http://ftp.uni-stuttgart.de/pub/systems/winxp/fixes/security-bulletins/usa/vm-sfix3.exe
Or delete Microsoft's Java VM and use Sun's, instead:
http://java.sun.com/j2se/1.4/download.html.
Sun's is said to be slower, but safer.
Or perhaps IBM's, which has a good reputation for high performance:
http://www7b.boulder.ibm.com/wsdd/wspvtdownload.html (newest)
http://www.ibm.com/developerworks/java/jdk/118/jre-info.html (stable)
e.1) If you run Windows XP, you should first disable its dangerous
"SSDP Discovery Service" (UnPnP) as described here:
http://grc.com/UnPnP/UnPnP.htm
Then install Windows XP Service Pack 1:
http://www.microsoft.com/windowsxp/pro/downloads/servicepacks/sp1/
(Note: despite what it says on that page, this service pack is for
both the "Home Edition" and the "Professional Edition" of Windows XP.)
Unfortunately, SP1 is huge, so downloading and installing it is
tedious if you only have a slow modem connection. But if you are
in a hurry, you can use this quick, stop-gap fix from Steve Gibson
for the worst of the bugs repaired by SP1:
http://grc.com/xpdite/xpdite.htm
However, you still should install SP1 as soon as you can.
e.2) If you run Windows 95/98/Me, and you "share out" your disk over
a network using passwords to limit access, you need to apply this fix,
for a bug that is exploited by the Opaserv virus:
http://www.microsoft.com/technet/security/bulletin/MS00-072.asp
f) If you are running Microsoft Outlook (as opposed to Outlook
Express) as your email client, then be sure to apply the latest
Outlook email security updates.
For Outlook 98, get:
http://office.microsoft.com/downloads/9798/Out98sec.aspx
For Outlook 2000, get:
http://office.microsoft.com/Downloads/2000/Out2ksec.aspx and then
http://www.microsoft.com/technet/security/bulletin/MS02-021.asp
For Outlook 2002, get:
http://www.microsoft.com/technet/security/bulletin/MS02-021.asp
g) Macro virus avoidance, Part 1: If you use Microsoft Office XP
(Word 2002, Excel 2002, etc.) then you should apply Office XP
Service Pack 2 (SP2), from:
http://office.microsoft.com/downloads/2002/oxpsp2.aspx
Unfortunately, this is a 15.5 MB download, about 1.5 hours by modem.
But it is the only MS Office update you need, so you can skip the
next paragraph's instructions for applying MS01-034 and MS02-031.
If you use Microsoft Word 97, Word 2002, or any version in between,
or Microsoft Excel 2002, then you should apply the latest available
Security Update and/or Cumulative Patch. It is not clear from
Microsoft's web site whether or not MS01-034 is included in MS02-031,
so I recommend applying both. First, everyone should apply MS01-034:
http://www.microsoft.com/technet/security/bulletin/MS01-034.asp
Then, if you have MS Office 2000 SR-1a or SP2, Office XP SP1, Word
2000, Word 2002, or Excel 2002, you should also apply MS02-031:
http://www.microsoft.com/technet/security/bulletin/MS02-031.asp
h) Macro virus avoidance, Part 2: The "97" and later versions of
Microsoft Word, Excel, PowerPoint and Access, and Microsoft Project
4.1 and later, include a feature to help protect against infection
by macro viruses. (Earlier versions don't support macros, so they
are naturally immune to this threat.) If you have the vulnerable
versions of any of these programs, you should make sure that the
protection feature is enabled. To enable the feature, start each
of the programs and then:
For "97" versions:
Tools -> Options -> General
check the Macro virus protection check box
then click OK
For more recent versions:
Tools -> Macro -> Security
select either Medium or High
then click OK
For more information about the "Macro Virus Protection" feature, see:
http://office.microsoft.com/assistance/9798/o97mcrod.aspx
However, that document contains one piece of bad advice. Discussing
how you should answer when prompted about how to handle a document
containing macros, it says:
Disable Macros You should choose this command if you are unsure
of the source of the document, but you still want to open it.
Enable Macros You should choose this command if you know who
created the document.
That advice is wrong, wrong, WRONG! Macro viruses infect documents
after they are created, without regard for who created them. So the
source of the document does not matter. You should ALWAYS answer
"Disable Macros," except for those rare files that you know require
macros to display properly (which is almost never the case for Word
documents).
i) Macro virus avoidance, Part 3: Do not send Microsoft Word .doc
files in email. Instead, save your file in "Rich Text Format" and
send the .rtf file. If you send .rtf files instead of .doc files,
the recipients need not worry as much about receiving macro viruses
from you, and .rtf files are usually more compact, too. (However,
a .doc file that has been renamed to have a .rtf extension can still
have macro viruses in it.)
j) Apply the latest Cumulative Patch for Windows Media Player:
http://www.microsoft.com/technet/security/bulletin/MS02-032.asp
k) "Share out" disk drives only sparingly over your network. Grant
only "read-only" access unless write access is really necessary,
and don't share out your system drive (probably C:) unless really
necessary. Viruses like Qaz, Klez, and others spread via network
shares, simply by opening and modifying program files on other
computers over the network.
l) To safely view a suspicious message in Outlook Express, without
opening it, right-click on the message summary line, then:
Properties -> Details -> Message Source...
To safely view a suspicious message in Outlook (not Outlook Express),
highlight the message summary line, then from the main program menu
bar at the top of the window:
File -> Save As...
change the Save as type... to Text Files (*.txt)
adjust the file name and location as desired
click Save
then open the saved .txt file in Notepad.
Or you can drag the message over to Outlook's "Tasks" folder and
examine it there, though that won't show the message body for HTML
formatted messages.
m) If you are a "techie" person doing "techie things," like
running a web server or using a VPN connection, you should also
read the advice of our friend, Mike McKee, here:
http://www.burtonsys.com/mike_advice.txt
-- they are executable
programs, regardless of the apparent file extension. Do not
open them!
c) There are some truly hideous bugs in Microsoft's email and
browser products, some of which let attached viruses run automatically
when the email is viewed either manually or in the "preview pane,"
even if Outlook Express is configured for the "Restricted Sites Zone."
Fortunately, Microsoft has fixes available, but that won't help you if
you don't have them. So, if you use Microsoft Internet Explorer 5.xx
or 6.0, and especially if you use Outlook or Outlook Express, it is
very important that you apply the latest security and "cumulative patch"
(formerly "security rollup") fixes.
The most important fix included in the latest "Cumulative Patch"
is MS01-020, which fixes a critical bug exploited by Klez. For
details of how that bug works, see microsoft_mime_bug.txt.
Note: for a nice table of older Microsoft security fixes, see:
http://www.zianet.com/bwd/securitybulletins.asp
Unfortunately, it is not very up-to-date.
If you use Internet Explorer 6.0, then you need to install the MS02-047
"Cumulative Patch." (See details below.)
If you use Internet Explorer 5.5, then you need to first make sure
that you have either SP1 or SP2 installed, then install the MS02-047
"Cumulative Patch." (See details below.)
If you use Internet Explorer 5.01 under Windows 2000, then you need to
first make sure that you have IE 5.01 SP2 installed, or Windows 2000 SP3
installed (which also installs IE 5.01 SP3). Then install the MS02-047
"Cumulative Patch." (See details below.)
If you use Internet Explorer 5.01 under any operating system other than
Windows 2000, you cannot use MS02-047, so you must instead use the
earlier MS02-015 "Cumulative Patch," (see details below). Or, better
yet, upgrade to Internet Explorer 5.5 or 6.0. But if you insist on
sticking with IE 5.01 under Win-9x/Me, first make sure that you have
IE 5.01 SP2 installed, then apply MS02-009 and MS02-015 (details below).
Note: Internet Explorer 5.00 and earlier are no longer supported by
Microsoft, and Internet Explorer 5.01 is only supported on Windows 2000.
However, if you are running IE 5.01 or IE 5.5, then you might need to
apply a "Service Pack" before you can apply the "Cumulative Patch."
Note: to check which service packs are already installed, start Internet
Explorer and click on Help -> About, and look at the "Update Versions"
line. If you see "SP1", "SP2" or "SP3" then you already have Service
Pack 1, 2 or 3, respectively, installed in your copy of Internet
Explorer.
If you are running IE 5.01, you must first apply Service Pack 2 (SP2),
unless it is already installed, before you can apply the Cumulative
Patch update. If you are running IE 5.5, you should first apply SP2
unless either SP1 or SP2 is already installed.
For IE 5.5, if you don't already have either SP1 or SP2 installed, then
get SP2 here:
http://www.microsoft.com/Windows/ie/downloads/recommended/ie55sp2/default.asp
or here: http://support.microsoft.com/default.aspx?scid=kb;en-us;Q276369
For IE 5.01, if SP2 is not already installed, then get it here:
http://support.microsoft.com/default.aspx?scid=kb;en-us;Q267954, or here:
http://www.microsoft.com/Windows/ie/downloads/recommended/ie501sp2/default.asp
For IE 6.0, there are no Service Packs (yet).
Then for IE 5.5 or IE 6, or for IE 5.01 under Windows 2000, apply
MS02-047 (a/k/a Q323759), about 2-2.5 MB (~8-15 minutes to download
with a typical dial-up modem):
http://www.microsoft.com/windows/ie/downloads/critical/q323759ie/default.asp
Or for IE 5.01 under Win-9x/Me or NT 4, apply MS02-009 (a/k/a q318089),
about 300 KB (~2 minutes to download with a typical dial-up modem):
http://www.microsoft.com/technet/security/bulletin/MS02-009.asp,
then apply MS02-015 (a/k/a Q319182), about 2-2.4 MB (~8-15 minutes
to download with a typical dial-up modem):
http://www.microsoft.com/technet/security/bulletin/MS02-015.asp
Note #1: Microsoft fixes should generally be applied in chronological
order, according to the dates on which they were released.
Note #2: Unless you are running Windows XP, when applying two or more
Microsoft fixes which prompt you to reboot the computer, you really
should let it reboot the computer after each one. Or, with NT 4 or
Windows 2000, you may apply them all and then run Microsoft's
QChain.exe utility before rebooting the computer. Get QChain here:
http://support.microsoft.com/default.aspx?scid=kb;EN-US;q296861
d) All Windows 9x/ME/NT/2K/XP users should apply these Microsoft
Java/VM updates:
http://www.microsoft.com/technet/security/bulletin/ms02-013.asp
http://www.microsoft.com/technet/security/bulletin/ms02-052.asp (Q329077)
MS02-013 is 4.3 MB. Fortunately, MS02-052 is only 168 KB, so it
is a quick download. Unfortunately, even though Microsoft says that
these fixes are "critical" for users of all versions of Windows
9x/Me/NT/2K/XP, they now seem to be only available through Microsoft's
cumbersome "Windows Update" facility (search for "Q329077"), which
only supports Windows 2000 & XP. There probably is some way for
Win 9x/Me users to get the fixes from Microsoft's web site, but I
haven't figured out how. Perhaps you can just lie about what version
of Windows you are using?
MS02-052 is apparently the same for all versions of Windows, and it
can also be downloaded as vm-sfix3.exe (Q329077) - 167,168 bytes from
http://ftp.uni-stuttgart.de/pub/systems/winxp/fixes/security-bulletins/usa/vm-sfix3.exe
Or delete Microsoft's Java VM and use Sun's, instead:
http://java.sun.com/j2se/1.4/download.html.
Sun's is said to be slower, but safer.
Or perhaps IBM's, which has a good reputation for high performance:
http://www7b.boulder.ibm.com/wsdd/wspvtdownload.html (newest)
http://www.ibm.com/developerworks/java/jdk/118/jre-info.html (stable)
e.1) If you run Windows XP, you should first disable its dangerous
"SSDP Discovery Service" (UnPnP) as described here:
http://grc.com/UnPnP/UnPnP.htm
Then install Windows XP Service Pack 1:
http://www.microsoft.com/windowsxp/pro/downloads/servicepacks/sp1/
(Note: despite what it says on that page, this service pack is for
both the "Home Edition" and the "Professional Edition" of Windows XP.)
Unfortunately, SP1 is huge, so downloading and installing it is
tedious if you only have a slow modem connection. But if you are
in a hurry, you can use this quick, stop-gap fix from Steve Gibson
for the worst of the bugs repaired by SP1:
http://grc.com/xpdite/xpdite.htm
However, you still should install SP1 as soon as you can.
e.2) If you run Windows 95/98/Me, and you "share out" your disk over
a network using passwords to limit access, you need to apply this fix,
for a bug that is exploited by the Opaserv virus:
http://www.microsoft.com/technet/security/bulletin/MS00-072.asp
f) If you are running Microsoft Outlook (as opposed to Outlook
Express) as your email client, then be sure to apply the latest
Outlook email security updates.
For Outlook 98, get:
http://office.microsoft.com/downloads/9798/Out98sec.aspx
For Outlook 2000, get:
http://office.microsoft.com/Downloads/2000/Out2ksec.aspx and then
http://www.microsoft.com/technet/security/bulletin/MS02-021.asp
For Outlook 2002, get:
http://www.microsoft.com/technet/security/bulletin/MS02-021.asp
g) Macro virus avoidance, Part 1: If you use Microsoft Office XP
(Word 2002, Excel 2002, etc.) then you should apply Office XP
Service Pack 2 (SP2), from:
http://office.microsoft.com/downloads/2002/oxpsp2.aspx
Unfortunately, this is a 15.5 MB download, about 1.5 hours by modem.
But it is the only MS Office update you need, so you can skip the
next paragraph's instructions for applying MS01-034 and MS02-031.
If you use Microsoft Word 97, Word 2002, or any version in between,
or Microsoft Excel 2002, then you should apply the latest available
Security Update and/or Cumulative Patch. It is not clear from
Microsoft's web site whether or not MS01-034 is included in MS02-031,
so I recommend applying both. First, everyone should apply MS01-034:
http://www.microsoft.com/technet/security/bulletin/MS01-034.asp
Then, if you have MS Office 2000 SR-1a or SP2, Office XP SP1, Word
2000, Word 2002, or Excel 2002, you should also apply MS02-031:
http://www.microsoft.com/technet/security/bulletin/MS02-031.asp
h) Macro virus avoidance, Part 2: The "97" and later versions of
Microsoft Word, Excel, PowerPoint and Access, and Microsoft Project
4.1 and later, include a feature to help protect against infection
by macro viruses. (Earlier versions don't support macros, so they
are naturally immune to this threat.) If you have the vulnerable
versions of any of these programs, you should make sure that the
protection feature is enabled. To enable the feature, start each
of the programs and then:
For "97" versions:
Tools -> Options -> General
check the Macro virus protection check box
then click OK
For more recent versions:
Tools -> Macro -> Security
select either Medium or High
then click OK
For more information about the "Macro Virus Protection" feature, see:
http://office.microsoft.com/assistance/9798/o97mcrod.aspx
However, that document contains one piece of bad advice. Discussing
how you should answer when prompted about how to handle a document
containing macros, it says:
Disable Macros You should choose this command if you are unsure
of the source of the document, but you still want to open it.
Enable Macros You should choose this command if you know who
created the document.
That advice is wrong, wrong, WRONG! Macro viruses infect documents
after they are created, without regard for who created them. So the
source of the document does not matter. You should ALWAYS answer
"Disable Macros," except for those rare files that you know require
macros to display properly (which is almost never the case for Word
documents).
i) Macro virus avoidance, Part 3: Do not send Microsoft Word .doc
files in email. Instead, save your file in "Rich Text Format" and
send the .rtf file. If you send .rtf files instead of .doc files,
the recipients need not worry as much about receiving macro viruses
from you, and .rtf files are usually more compact, too. (However,
a .doc file that has been renamed to have a .rtf extension can still
have macro viruses in it.)
j) Apply the latest Cumulative Patch for Windows Media Player:
http://www.microsoft.com/technet/security/bulletin/MS02-032.asp
k) "Share out" disk drives only sparingly over your network. Grant
only "read-only" access unless write access is really necessary,
and don't share out your system drive (probably C:) unless really
necessary. Viruses like Qaz, Klez, and others spread via network
shares, simply by opening and modifying program files on other
computers over the network.
l) To safely view a suspicious message in Outlook Express, without
opening it, right-click on the message summary line, then:
Properties -> Details -> Message Source...
To safely view a suspicious message in Outlook (not Outlook Express),
highlight the message summary line, then from the main program menu
bar at the top of the window:
File -> Save As...
change the Save as type... to Text Files (*.txt)
adjust the file name and location as desired
click Save
then open the saved .txt file in Notepad.
Or you can drag the message over to Outlook's "Tasks" folder and
examine it there, though that won't show the message body for HTML
formatted messages.
m) If you are a "techie" person doing "techie things," like
running a web server or using a VPN connection, you should also
read the advice of our friend, Mike McKee, here:
http://www.burtonsys.com/mike_advice.txt
IV. FREE VIRUS REMOVAL AND PROTECTION TOOLS:
The most common viruses/worms going around right now seem to be
Klez/ElKern/Foroux, Bugbear, Magistr, Yaha/Lentin, Sircam, Goner,
Badtrans, Qaz, and Hybris. There are free removal tools available
for all nine of these, and for many other viruses.
This site has a quite comprehensive list of virus removal tools:
http://virusall.com/downrem.html
Symantec/Norton has many free virus removal tools, including tools
for removing Bugbear, Sircam, Goner, Badtrans, Hybris, Nimda, Qaz,
Kriz, the most common Klez/ElKern variants, Yaha (Lentin), and
several others (but not Magistr or CIH/Chernobyl), here:
http://www.symantec.com/avcenter/tools.list.html
McAfee/NAI also has a few, here:
http://www.mcafeeb2b.com/naicommon/avert/avert-research-center/tools.asp
Sophos also has some, including free Magistr, CIH/Chernobyl, and
Yaha/Lentin removal tools:
http://www.sophos.com/support/disinfection/
Gibson Research has a CIH/Chernobyl recovery tool, here:
http://grc.com/cih.htm
Kaspersky has a free tool to remove Klez, Sircam and Goner, here:
ftp://ftp1.avp.ch/utils/clrav.com
Cat Computer Services has free removal tools for Klez.h, CIH/Chernobyl,
and some others, here:
http://www.quickheal.com/othdown.htm
Note: Klez.h (and some other Klez variants) are sometimes identified
as Klez.gen.
SRN Micro (Solo AntiVirus) and Prognet (Fire AntiVirus) are closely
related companies, with similer web sites but somewhat different
selections of free virus removal tools. They offer free tools to
remove Klez, Badtrans, Sircam, Kriz, CIH/CHernobyl, Goner, and some
others, here:
http://www.srnmicro.com/downloads/ or
http://fireav.com/downloads/ or
http://www.antivirus-download.com/downloads/
BitDefender has free removal tools for Klez, Kriz, Magistr, Sircam,
Qaz, Badtrans, and others, here:
http://www.bitdefender.com/html/free_tools.php
Trend Micro has free removal tools for Klez, Goner (tool & instructions),
and Sircam (tool & instructions); enter the virus name in the search
box on their web site: http://www.trendmicro.com
eScan/Microworld and F-Secure also have free Klez removal tools, here:
http://www.mwti.net/form.asp?url=free.asp
ftp://ftp.europe.f-secure.com/anti-virus/tools/kleztool.zip
Note: there are many variants of Klez; the free removal tools might
not remove all of them.
"The Cleaner" is a product which claims to be able to remove many
kinds of worms & viruses, including Magistr. It has a 30 day free
trial period: http://www.moosoft.com/
Also, one or more of the free general-purpose anti-virus packages
can probably remove your virus infection.
Yes, you read that correctly! Some of the less well-known
general-purpose anti-virus packages can be had for free, for home
use. They appear to be very credible alternatives to the expensive
big two (Norton & McAfee):
http://www.grisoft.com/
http://www.frisk.is/f-prot/download/ (DOS version is free)
http://www.free-av.com/
Plus these, which require a web connection when you use them:
http://www.pandasoftware.com/activescan/com/
http://housecall.antivirus.com/
http://security.norton.com/us/intro.asp?venid=sym&langid=us
and some others listed at http://virusall.com/downscan.html
Plus, many of the non-free anti-virus utilities have free 25-day
or 30-day demo versions or shareware versions available. Some are
available at the manufacturers' web sites, such as NOD32 from Eset,
and Solo AntiVirus from SRN Micro:
http://www.nod32.com/scriptless/download/trial.htm
http://www.srnmicro.com/downloads/evaluate/TrySolo.exe
Others are at the usual shareware web sites. E.g., Tucows has
demos for F-Secure, Norton, Kaspersky, eScan, Panda, and others:
http://www.tucows.com/system/virus95.html
But don't get "Admiral VirusScanner" or "In Vircible Anti virus"
because they are "spyware" -- see the usual spyware list sites:
http://www.spychecker.com/ & http://www.tom-cat.com/spybase/spylist.html
(Note: "spyware" is similar to "scumware" -- you don't want it.)
Note: Real anti-virus tools do not show up in your email mailbox
as unsolicited file attachments. So don't be fooled! One of the
Klez variants tries to induce you to run it by claiming to be an
antidote to, of all things, the Klez.E worm/virus. It says:
NOTE: Because this tool acts as a fake Klez to fool the
real worm,some AV monitor maybe cry when you run it.
If so,Ignore the warning,and select 'continue'.
That is a lie. The email attachment is the virus/worm. Don't run it.
VII. REMOVING THE KLEZ.H VIRUS:
This section is for people whose computers are already infected
with a Klez virus (probably Klez.H, which is also sometimes
identified as Klez.gen, Klez.G, or Klez.I). If, instead, you
need to find out the source of a Klez-infected email, see above.
This is the Symantec/Norton info about this virus:
http://securityresponse.symantec.com/avcenter/venc/data/w32.klez.h@mm.html
This is the Sophos info about this virus:
http://www.sophos.com/virusinfo/analyses/w32klezh.html
This is the F-Secure info about this virus:
http://www.f-secure.com/v-descs/klez_h.shtml
Note: Most people who get the Klez.H virus get it because they
are using an unpatched (buggy) version of Microsoft Outlook
Express to read email. So after you remove the Klez.H virus,
be sure to follow the instructions above to install the latest
Microsoft fixes and setting changes for Outlook Express and
Internet Explorer. Or delete Outlook Express from your computer
and just use a Yahoo account for email! (For details about how
the Outlook Express/IE bug works, see microsoft_mime_bug.txt.)
If you have an anti-virus tool like Norton Anti Virus ("NAV")
but can't get it to install, the reason is probably that Klez
is already running, and it blocks many anti-virus tools from
starting. You might be able to get your AV tool to work if you
shut down the computer, turn the power off, wait 30 seconds (to
clear RAM memory), and then start up the computer in "safe mode"
before trying to run the AV tool.
Note: If you are running Windows Me or Windows XP, then you
should also disable its "System Restore" feature before
shutting down. For how to do so under Win-Me, see:
http://service2.symantec.com/SUPPORT/tsgeninfo.nsf/docid/2001012513122239
For how to disable System Restore under Win-XP, see:
http://service4.symantec.com/SUPPORT/tsgeninfo.nsf/docid/2001111912274039
But the easiest way to remove the virus is probably to run
one of the tools that is specifically designed to remove
this particular virus. There are at least six different
free Klez free removal available from various AV software
vendors. Most are quite small, so you could download
several of them onto a single diskette, and still have room
to spare.
I don't know for certain which Klez removal tool is best,
but www.techtips4u.com says that it is Symantec's:
http://securityresponse.symantec.com/avcenter/venc/data/w32.klez.removal.tool.html
Cat Computer Services has one which I'm told sometimes works
even when the Symantec and Kaspersky tools fail:
http://www.quickheal.com/killklez.htm
Kaspersky also has a simple one (also available from F-Secure):
ftp://ftp1.avp.ch/utils/clrav.com or
ftp://ftp.europe.f-secure.com/anti-virus/tools/kleztool.zip
I recommend that you download the Symantec/Norton tool, the CAT
Computer Services tool, and the Kaspersky tool onto a diskette,
then write-protect the diskette and take it to the infected
computer. Then follow the instructions and run the Symantec tool
first. If it fails then run the CAT tool. Then reboot and run
the Kaspersky tool to verify that the Symantec or CAT tool
successfully removed the virus.
(For links to some other free Klez removal tools, see
section IV, above.)
Note #1: if you have several computers networked together, then
you need to first disconnect the network (or power-off the
hub). Then run the virus removal tool on every Windows
computer on your network before reconnecting the network.
Otherwise, Klez is likely to immediately reinfect your freshly-
disinfected computers, via your network.
Then go back and read the rest of this document, so you can
learn how to avoid future virus infections!
Note #2: I recommend that you back up your critical document
and data files before disinfecting your computer. I recently
helped someone remove Klez.H from her Windows-Me computer using
the Kaspersky tool, and when she was done the computer would no
longer boot, not even in "safe mode." I think this is unusual,
but to recover we had to boot Windows-Me from the Installation
CD, delete several files from the Windows system directory, and
reinstall Windows-Me. (Her computer dealer had wanted to reformat
the hard disk drive!) She didn't end up losing any important
files, but recovering it cost us a lot of time and aggravation.
BTW, to enable Win-Me to reinstall, the files we deleted from the
c:\windows directory were user.dat, system.dat, classes.dat and
wininit.ini, per http://www.techtips4u.com/ostt/installsafe.htm
and http://www.servenet.com/ipiboard/archive010601/3927.html
-Dave Burton <dburton@burtonsys.com>
Burton Systems Software: http://www.burtonsys.com/
Tel: 1-919-481-0149